An Italian.. Ransomware?
2024.05.09 · Analysis and study of Italian .NET Windows ransomware.
While exploring the any.run malware analysis platform in search of new threats to study, I came across something particularly unusual.
Using search filters to select Italy as the country of interest and files executed in a sandbox environment, a file marked as ransomware immediately caught my attention.
First steps
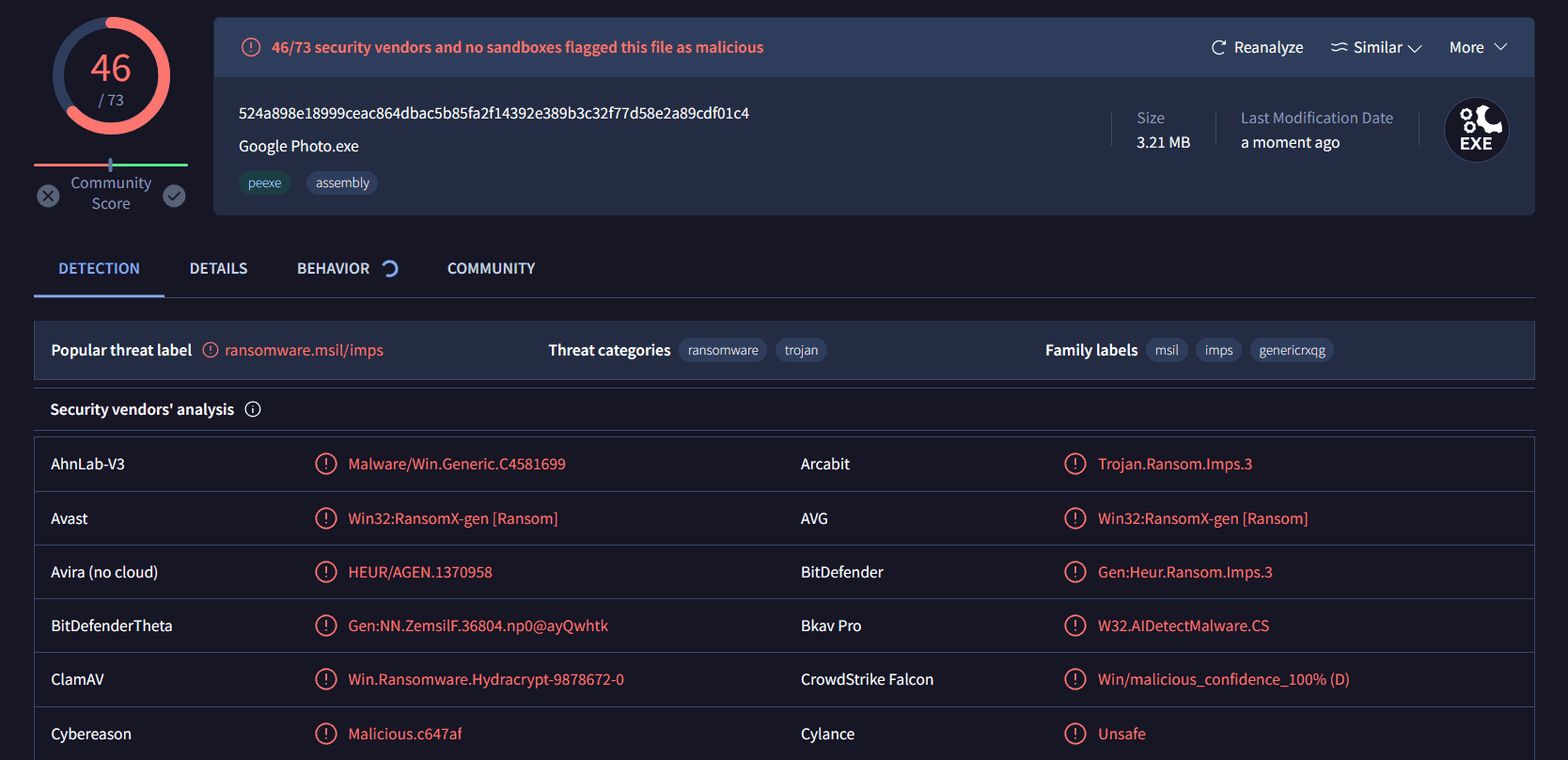
The first thing I did after downloading the sample ("Google Photo.exe") was to analyze the file on VirusTotal. As expected, most antivirus software detects the file as malicious.
Preliminary analysis
As is standard practice, I used Detect it easy to obtain additional information about the executable.
This tool provided me with valuable details, including the programming language used to develop the file, the version of the compiler used, and the version of the operating system targeted by the malware.
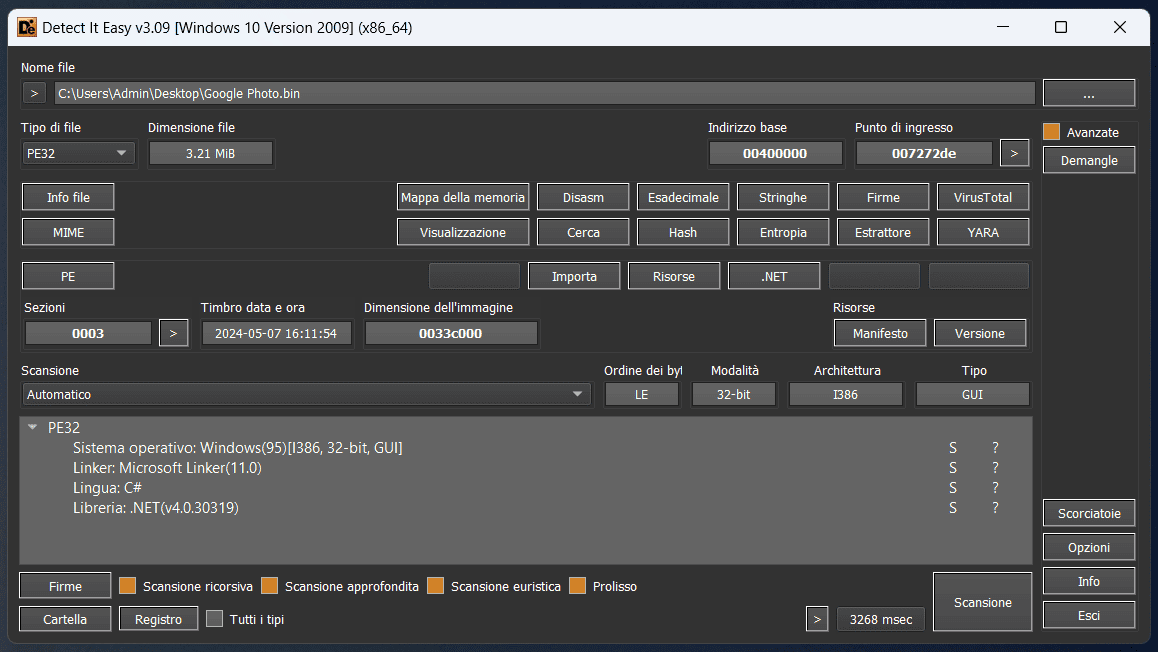
The analysis revealed that the program was compiled using the .NET 4.0 framework in AnyCpu mode.
This development choice suggests that the ransomware may have been written in Visual Basic or C#. The decision to use the .NET 4.0 framework is considered clever, to say the least, as this version is pre-installed and pre-activated on all Windows operating systems starting with XP.
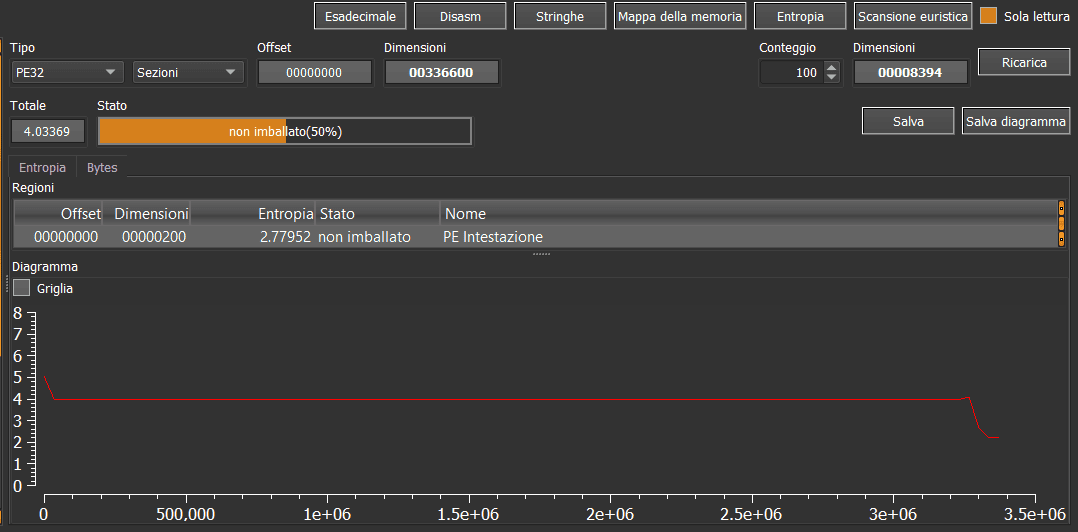
Analysis with Detect it easy revealed that the file was probably not compressed (packed), as suggested by the data entropy.
Reverse Engineering
Once I had a detailed view of the executable and considering that it was compiled using the .NET framework, I used DnSpyEx to decompile the file and access the code entry point.
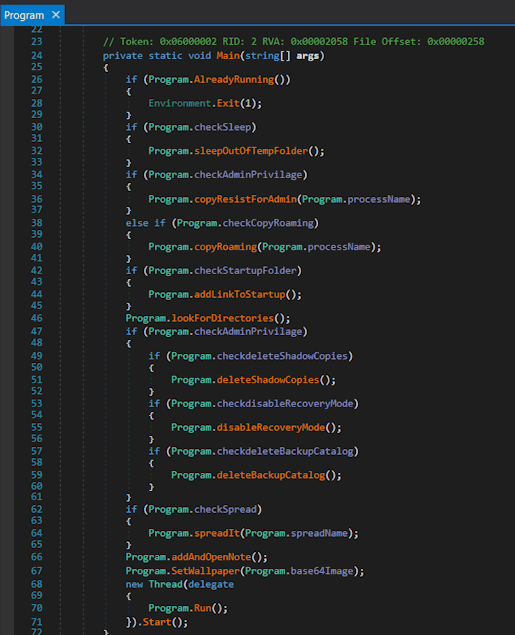
It would appear that the executable has not been subject to obfuscation techniques.
Analysis of the function names clearly suggests their purpose and operation, leaving no room for significant doubt.
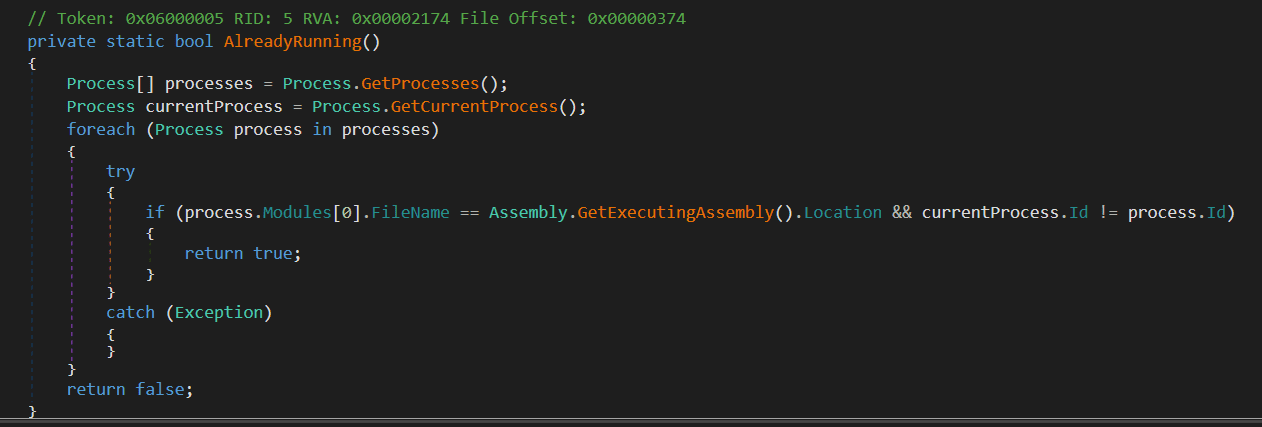
This feature, although relatively simple, has limited effectiveness. Its task is to check the main image of all running processes. However, it only compares the path of the ransomware executable with that of active processes. This approach does not take into account possible variations in the file names or save paths of the ransomware, which could lead to false negatives.